Malwarebytes Browser Guard:
Beyond Ad Blocker
$35.99 value FREE!
Concerned about scams and ad trackers? Annoyed with ads?
Try our free ad blocker for a safer and cleaner web surfing experience.
Works with Chrome, Edge, Firefox and Safari browsers.
Browser Guard for Safari is available on the App Store for Mac
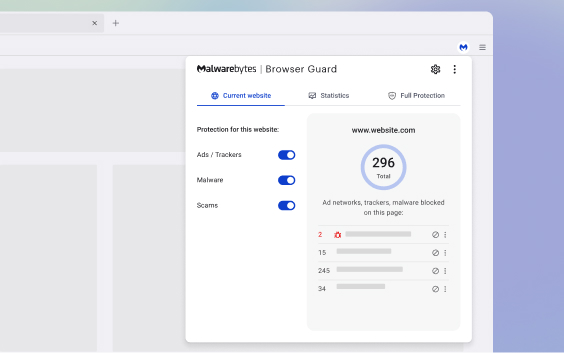
Browser ad blocker
that also beats the
scammers
Malwarebytes Browser Guard crushes unwanted and unsafe content, giving you a safer and faster browsing experience. Not only that, it is the world’s first browser extension that can identify and stop tech support scams. We take on the bad guys so you don’t have to.
Crushes ads
Removes annoying ads that often point to content of questionable value.
Protects your privacy
Blocks third-party ad trackers that follow you around the Internet and target you with the same ads over and over again.
Stops malware in your browser
Blocks web pages that contain malware, stops in-browser cryptojackers (unwanted cryptocurrency miners), and gives other malicious content the boot.
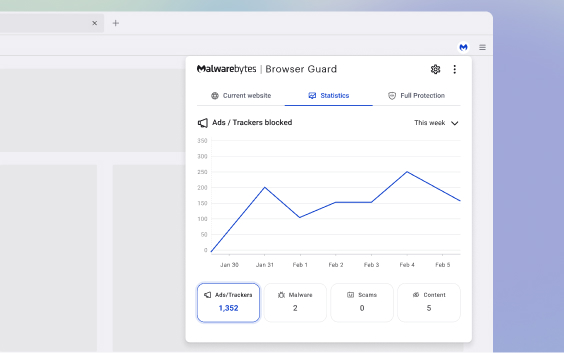
Browse up to 4x faster
Speeds up how fast web pages display by blocking third-party ads and other unwanted content, saving your sanity and bandwidth.
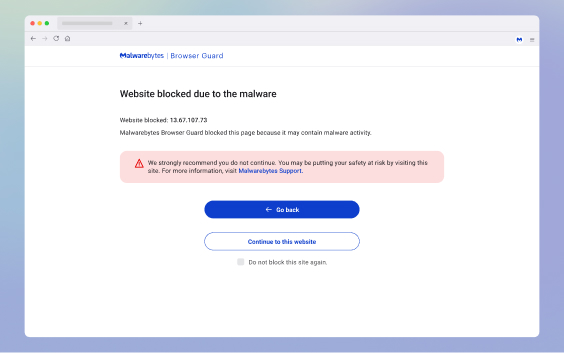
Puts the hurt on tech support scammers
Identifies and stops browser lockers, browser hijackers, and other scare tactics tech support scammers use to con you out of money.
A $35.99/year value, FREE for everyone.
Malwarebytes Browser Guard is a FREE product that provides industry-leading ad, scam and tracker blocking that other companies charge annual fees for.
Additionally, all of our Malwarebytes paid plans come with Browser Guard and include extra features for Windows devices.
Download for Safari on the Mac App Store
Don’t take our word for it
“Like it. Have not gotten a single ‘Tech Support’ browser lock since installing this. Saved what little is left of my sanity.”
“I use these on multiple browsers. It works great, especially at preventing me from visiting websites that have Trojans and crypto hidden in them.”
“This is the best browser safety extension by a country mile, in comparison to the others this one actually works and on top of that it doesn’t slow you down—5/5. A fantastic Add-on.”
Tech specs
Supported browser
Available for Chrome, Edge, Firefox, Safari (macOS12.0 or higher only)
Desktop Only
Languages supported
English, German, Spanish, French, Italian, Polish, Dutch, Portuguese (Brazil), Portuguese (Portugal), Russian
Now Browser Guard* comes with some exclusive features for Premium users on Windows:
Content Control: Dial up your control of your browsing experience and define what’s appropriate for you, or not. Fully customize the content you want to block while you – or your kids – are surfing. Your time is precious, set your own boundaries and truly enjoy what matters to you online.
Import and Export: Global settings are here! Now your preferences and customized rules can work with all your browsers – even on other devices. Experience a consistent and clean web experience – Discover on this video how to Transfer Malwarebytes Browser Guard settings to another browser
Historical Detection Statistics: Ever wanted to go back in time and see what you avoided? Now you can! Learn more about the past detections and see what we’ve protected you from.
*Chrome, Firefox, Edge: You are automatically entitled to it with an active subscription to Malwarebytes Premium for Windows.
FAQs
What is Malwarebytes Browser Guard?
Get started
Download Malwarebytes Browser Guard today.